Patch Diffing In The Dark: Windows Vulnerability Research - A CVE Guided Approach

Upcoming Course Offering
- 📅 Browse Upcoming Events — Find the next in‑person or virtual session that fits your schedule.
Patch Diffing in the Dark Radar
Explanation: Patch Diffing in the Dark is weighted toward Vulnerability Research (90) and advanced Skill Level (90). It sharpens reverse engineering into a practical tool for analyzing CVEs and discovering modern vulnerabilities. It teaches you to systematically apply patch diffing and reverse engineering—using only free tools like Ghidra, WinDbg, and Sysinternals—to locate security-critical code changes in real-world Windows CVEs.
To find out which course is right for you, check out our training pathways.
OVERVIEW
This course teaches comprehensive Windows vulnerability research through a CVE-guided approach, using a rich ecosystem of open-source and freely available tools. Students will master reverse engineering, patch diffing, and vulnerability analysis with Ghidra, WinDbg, Sysinternals, and dynamic Windows RE utilities—no costly licenses required. You'll learn to dissect real-world CVEs using the same tools trusted by professional researchers and security teams.
The course reveals that you already have the resources and tooling needed to become an effective vulnerability researcher today. Through hands-on labs and guided analysis, students will build the confidence and competence to systematically research, analyze, and exploit complex Windows vulnerabilities.
This intensive, hands-on training is built on the three fundamental pillars of vulnerability research. You will master how to:
- Vulnerability Discovery: Use patch diffing and reverse engineering to systematically uncover security-critical code changes.
- Root Cause Analysis: Move beyond the surface to deeply understand the underlying technical causes of vulnerabilities and their corresponding classes.
- Exploit Development: Develop proof-of-concept exploits to trigger and demonstrate vulnerabilities.
We use real-world CVEs as our guide—our "north stars"—to navigate the entire vulnerability lifecycle. You will learn to leverage free and powerful tools in a lab-driven environment, building not just your skills, but your confidence to tackle complex vulnerabilities on your own.
ABSTRACT
This fast-paced training teaches comprehensive vulnerability research on Windows platforms using real CVEs as case studies. Starting with CVE descriptions, you'll progress through patch diffing and reverse engineering to achieve complete understanding of vulnerability root causes, culminating in practical exploit POC development.
The hands-on curriculum combines topical lessons with practical exercises covering recent Windows CVEs and their binaries. You'll master the patch diffing workflow, learn systematic approaches to modern vulnerability research, and acquire research best practices while avoiding common pitfalls.
The training's accessibility is its most valuable aspect. Using free tools (Ghidra SRE framework, BinDiff, WinDbg) and readily available CVE information, you'll discover how to analyze complex vulnerabilities through both static and dynamic techniques. Participants learn to leverage CVEs as guides for reverse engineering and vulnerability research, transforming from knowing about vulnerabilities to actually understanding them.
Why CVEs?
CVEs serve as documented learning guides that navigate the complete vulnerability research lifecycle. They provide benchmarks showing what constitutes modern Windows vulnerabilities, setting real-world security research standards.
“It’s almost as if variant analysis and patch diffing is useful.”
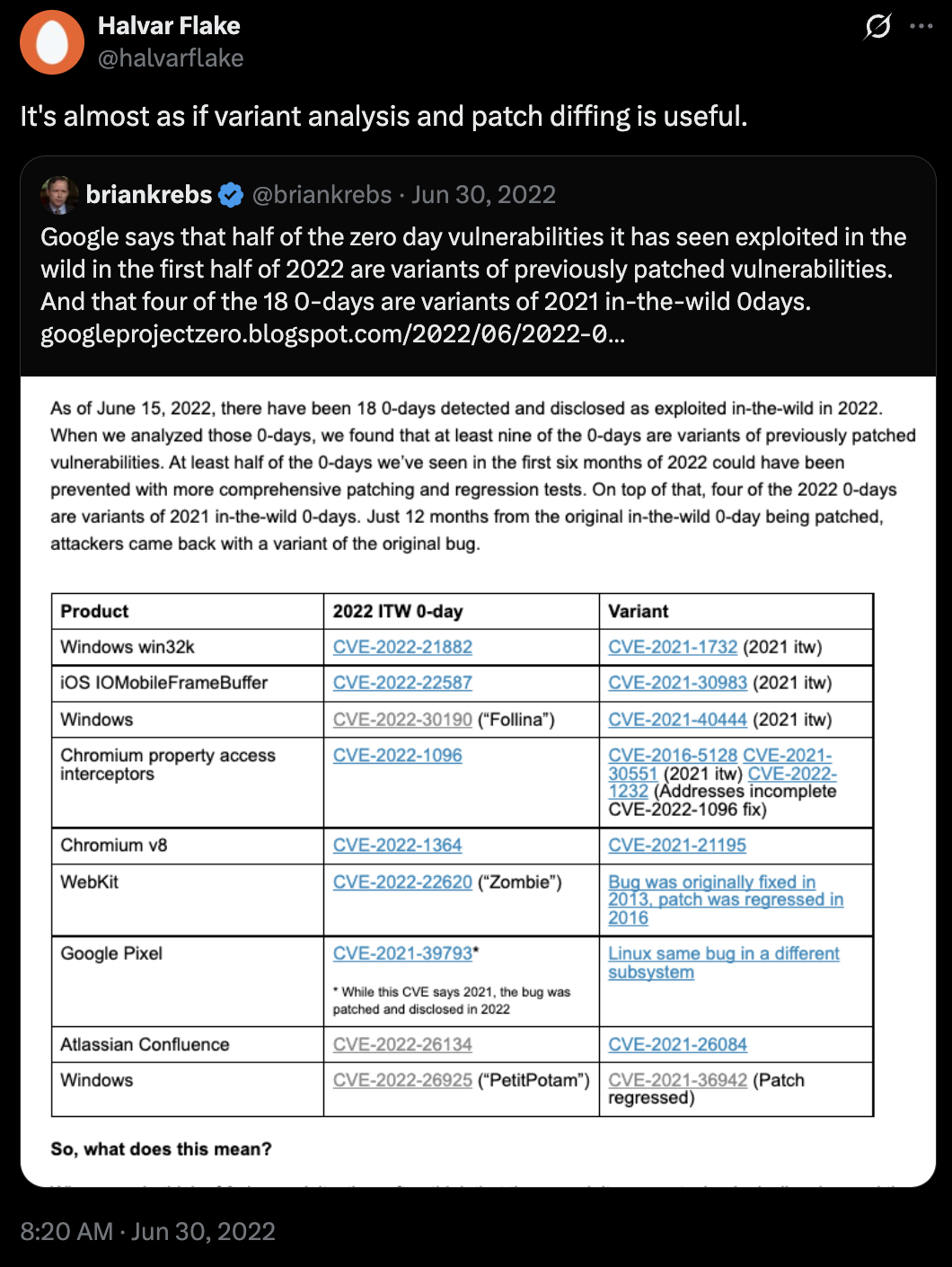
For beginners, this CVE-guided methodology offers crucial context about the complexity, impact, and technical depth needed to identify vulnerabilities that matter in today's threat landscape. Advanced researchers gain insights into emerging vulnerability patterns and attack surfaces while developing a systematic framework for approaching new research areas with confidence and methodological rigor.
WHO SHOULD ATTEND
- Cybersecurity Professionals seeking to advance their skills in reverse engineering complex vulnerabilities to mitigate risk and evaluate recent CVEs.
- Vulnerability Researchers looking to learn a practical and systematic methodology for vulnerability discovery and analysis.
- Reverse Engineers wanting to understand how modern operating systems are compromised through vulnerable applications and services.
- Defenders aiming to proactively analyze patches and understand 1-day vulnerabilities to improve detection and defense strategies.
- Red Team / Penetration Testers wanting to master the skill of finding and weaponizing N-day vulnerabilities when public exploits are not available.
KEY LEARNING OBJECTIVES
- Master the CVE-to-Root Cause Workflow: Systematically analyze any CVE from its initial description through to a deep understanding of its technical root cause.
- Perform Advanced Patch Diffing: Confidently use binary diffing tools to pinpoint security-critical changes between software versions.
- Identifying Vulnerabilities: Develop the ability to identify software flaws through comparative analysis, informed by common vulnerability classes.
- Conduct In-Depth Binary Analysis: Employ static and dynamic reverse engineering techniques to map attack surfaces and identify vulnerable code paths.
- Develop Proof-of-Concept Exploits: Translate vulnerability knowledge into working PoCs to verify impact and demonstrate exploitability.
- Leverage AI Tools for Exploit Development: Use modern AI assistance to kickstart and accelerate POC exploit development, enhancing research efficiency.
- Utilize a Modern Toolchain: Become proficient in using and integrating free, powerful tools like Ghidra, BinDiff, Ghidriff, and WinDbg into your research workflow.
PRACTICAL EXERCISES
Patch Diffing and Root Cause Analysis of real world CVEs
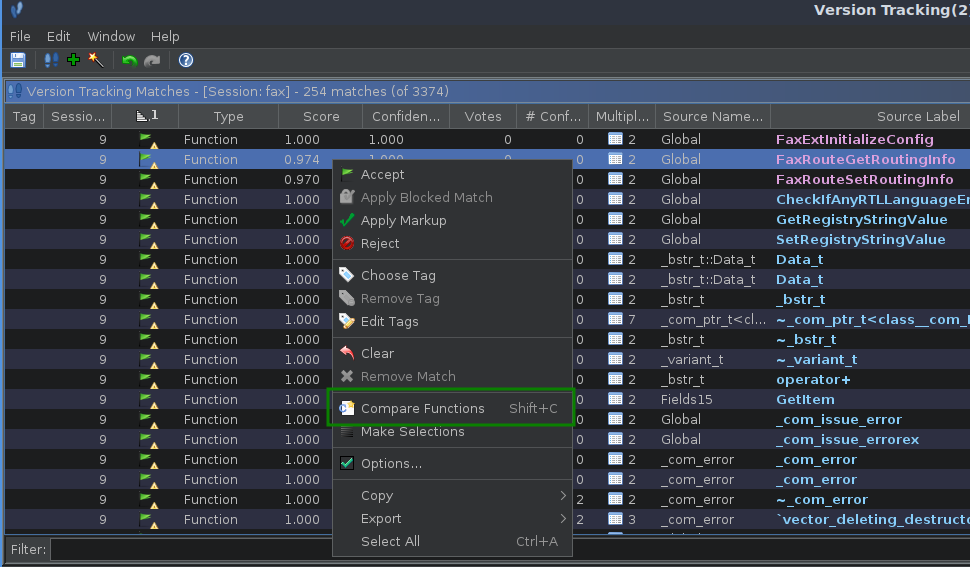
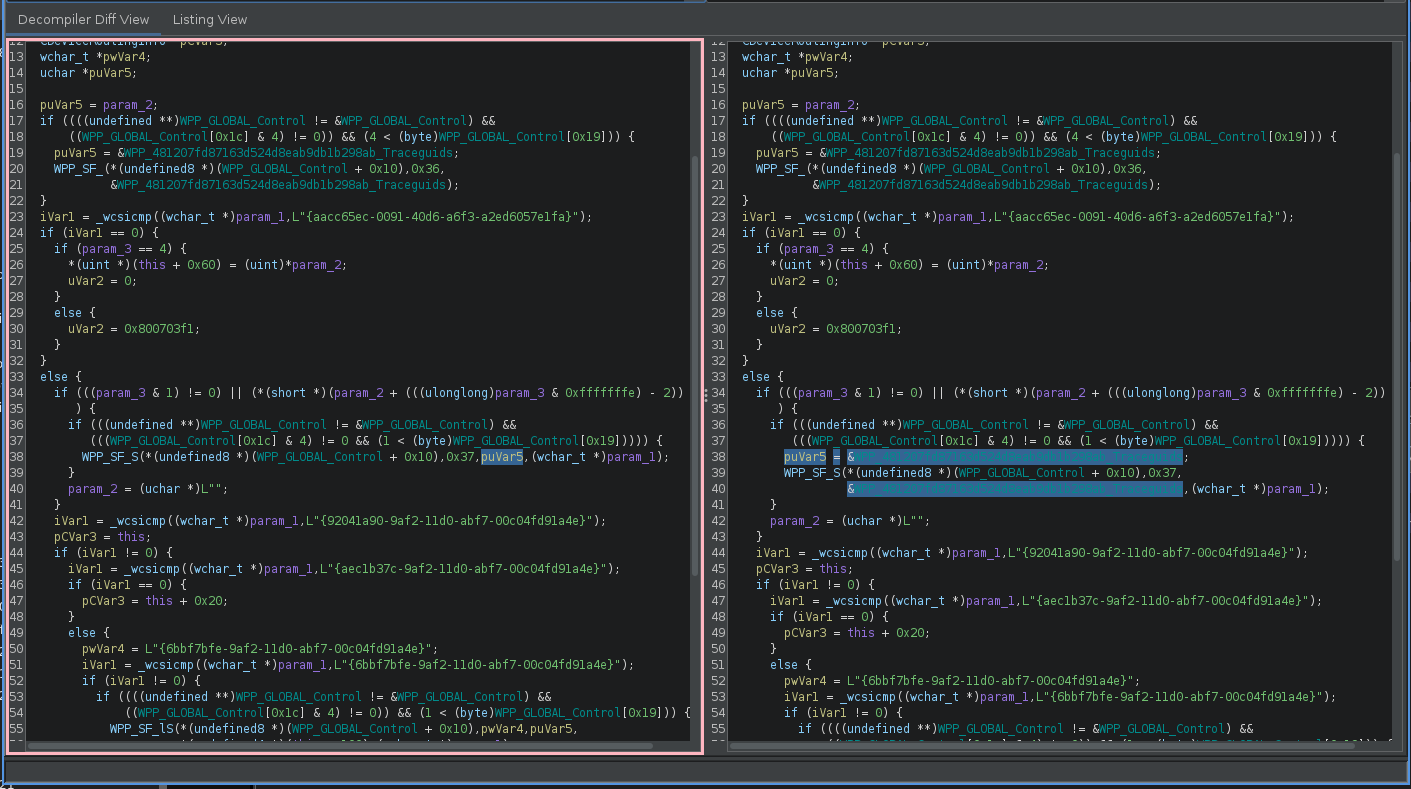
- Use patch diffing to compare vulnerable and patched Windows binaries, systematically identifying security-critical code changes
- Perform comprehensive root cause analysis to understand vulnerability classes and exploitation mechanics
Combined Static and Dynamic Analysis
- Utilize static analysis to identify security vulnerabilities and locate problematic areas of code.
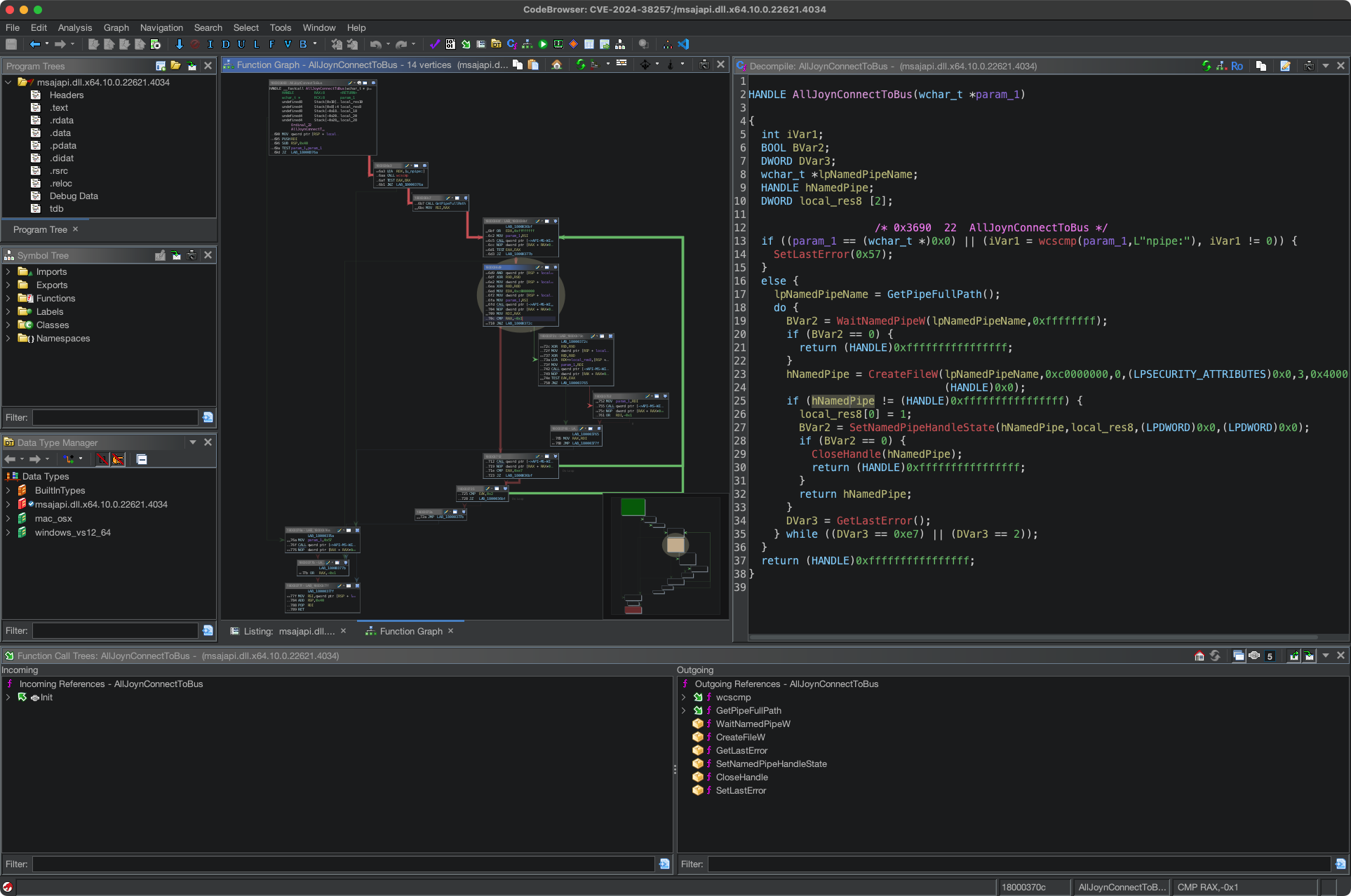
- Employ dynamic analysis with debuggers and third-party tools to deeply investigate CVEs and verify root causes.
- Learn to pivot from static to dynamic analysis with WinDbg, covering both user‑mode and kernel‑mode debugging
Building Exploit Proofs of Concept (POCs)
- Develop exploit POCs to demonstrate discovered vulnerabilities.
- Integrate AI-assisted code generation to streamline POC creation and refinement
COURSE DETAILS
Part 1 - Vulnerability Discovery Through Static Analysis
Master the foundational tools and techniques for systematic vulnerability discovery. Learn to leverage modern SRE platforms and patch diffing methodologies to identify security-critical code changes and uncover vulnerabilities in Windows binaries.
- Introduction
- Binary Diffing Use Cases & The Search for Binary Truth
- Overview of Target CVEs
- Introduction to the Toolchain (Ghidra, WinDbg)
- Reverse Engineering Windows Binaries
- A Ghidra Primer for Windows RE
- Leveraging Custom Data Types and Symbols
- Patch Diffing
- The Diffing Tools: Version Tracking, BinDiff, Ghidriff
- Mastering the Step-by-Step Patch Diffing Workflow
- Interpreting Diff Results
- Patching Holes in Ghidra Version Tracking
- Vulnerability Analysis - Static
- Discovering the Vulnerable Code Path
- Static Root Cause Analysis and Vulnerability Identification
- Automating Analysis with Ghidra Scripting
Part 2 - Dynamic Vulnerability Analysis and Classification
Transition from static to dynamic investigation. Develop expertise in constructing analysis environments, recognizing modern vulnerability classes, and employing dynamic analysis to validate and deepen your understanding of discovered vulnerabilities.
- Setting up the Dynamic Environment
- Rapid Deployment of Isolated Test Environments
- Configuring WinDbg,Sysinternals Suite, other analysis tools
- Understanding Vulnerability Classes
- Deep Dive into UAF, Info Leaks, Heap Overflows, etc.
- How to Recognize Vulnerability Patterns in Real-World Code
- Advanced Dynamic Analysis
- Pivoting from Static to Dynamic Analysis (learn both user and kernel mode debugging)
- Controlling Program State to Reach Vulnerable Code
Part 3 - Exploit Development - Attacking Windows Services
Apply your research skills to real-world Windows service exploitation. Develop end-to-end capabilities, from vulnerability discovery through to building a proof-of-concept that triggers the vulnerability.
- Foundations of Exploit POCs
- Building the vulnerable Test Environment
- Reverse Engineering the Target Service
- Finding vulnerable code paths
- Accelerating PoC Development
- "Patch Diffing in the Light": Leveraging Public PoCs
- Using AI Tools to Kickstart Exploit Code
- Building Trigger PoCs for Several Vulnerability Classes
Part 4 - Putting it All Together
Synthesize all acquired skills through a comprehensive final project designed to prepare you for real-world vulnerability research scenarios.
- Final Project (CTF Challenge)
- Identify the Vulnerable Application
- Research and Develop Code Paths
- Perform Full Static & Dynamic Analysis
- Develop a Final Exploit Trigger PoC
- Live "Grab Bag" CVEs (Time Permitting)
- Instructor-led walk-through of recent patch diffs on new or student-suggested CVEs.
- Experience will be unique for each class.
Student Requirements
This course is rated intermediate, but suitable for beginners with heart.
Suggested Prerequisites
- Basic Knowledge of Vulnerabilities or CVEs: Understand how the Common Vulnerabilities and Exposures (CVE) system identifies unique vulnerabilities and understand the concept of vulnerability classes.
- Understanding of Security Principles: A foundational grasp of cybersecurity concepts and practices.
- Assembly Language Basics: An introductory understanding of assembly language or familiarity with programming in C.
No prior experience with Ghidra is required.
What Students Will Be Provided With
- Course slides / Training materials
- Virtual machines with all the labs
- Resources for further learning
- Access to course CTF server during and beyond the course
- Access to instructor(s) via Discord during the course and beyond
Laptop Requirements
- 64-bit i7+ Laptop with 16GB+ RAM (ARM currently not supported)
- ~90 GB disk space (1 course and 2 target VMs)
- Ability to run Intel based VM running modern Windows 11
- VMware
Practical Takeaways
By the end of this course, participants will walk away with:
- A systematic CVE-to-Root Cause workflow for analyzing vulnerabilities from CVE description to technical deep dive
- Proficiency in advanced patch diffing techniques using free tools like BinDiff and Ghidriff to identify security-critical binary changes
- Hands-on expertise in static and dynamic binary analysis with Ghidra and WinDbg, including scripting for automation and kernel/user-mode debugging
- Deep understanding of modern vulnerability classes (e.g., UAF, heap overflows, info leaks) and how to recognize them in real-world Windows code
- Practical skills in building proof-of-concept exploits, accelerated by AI tools for code generation and refinement
- A configured dynamic analysis lab environment with Sysinternals Suite and isolated Windows test setups for safe vulnerability testing
- Completion of a capstone CTF project demonstrating full-cycle vulnerability discovery, root cause analysis, and exploit development on a custom challenge
- Access to reusable course materials, virtual machines, and ongoing community support via Discord for tackling live CVEs
Upcoming Courses
- 📅 Browse Upcoming Events — Find the next in‑person or virtual session that fits your schedule.